Introduction
eCommerce websites are a very profitable and relatively easy way for Small to Medium Businesses to make a profit. These websites are portals that help promote a company’s brand and products as well as a good resource to collect customer feedback. This means these websites are gathering data about the visitors, shopping behaviors. At the same time, protecting your eCommerce security along with the safety of the clients should be a top priority.
Large eCommerce companies have the luxury of affording their own in-house IT departments and security departments but not everyone has the resources to do that. Startups and SMBs have limited budgets and resources, which leaves cybercriminals with a chance to take advantage of this vulnerability. You can do penetration testing to see if your website is vulnerable or not.
The new malware trend aimed towards automation of attacks puts these businesses even more in danger. Hackers automate their threat software and attack large numbers of corporate and eCommerce websites instead of attacking them one at a time. This puts a huge target on SMBs as they become a field of opportunity for cyber attackers because of the data they collect – especially if they use a virtual data room – and the lack of protection they have.
Even if you run security checks on a regular basis and find no problems, you should never relax. Online fraud is rapidly developing, and a single small flaw may result in your efforts being wasted. This is why it’s important to prioritize website protection and be aware of the most common types of eCommerce threats.
- Introduction
- Best Practices and Steps for Ecommerce Security
- Step 1: Promote the use of strong, unique passwords
- Step 2: Use HTTPS hosting
- Step 3: Protect your devices
- Step 4: Defend yourself against attempts at social engineering
- Step 5: Protect your domain with email authentication protocols
- Step 6: Implement additional authentication
- Step 7: Keep useful information about your customers
- Step 8: Make sure your website is up to date
- Step 9: Review all plugins and third-party integrations on a regular basis
- Step 10: Backup your data
- Step 11: Make sure your customer service team is ready
- Step 12: Prepare a security update strategy
- Conclusion
Best Practices and Steps for Ecommerce Security
To begin with, eCommerce website protection refers to several actions and initiatives that protect your website from attacks and ensure the security of your online transactions.
In fact, your online store is a complex system with numerous components that must communicate with one another, including your server, web apps, customers, and network connection. The most important thing is that you should secure each part against threats and malicious attacks. By the way, you can also use storage as a service, which is a data storage business model.
Even if your site, server, and account are all safe, criminal activity can still occur: keyloggers and spyware installed on your customers’ computers allow criminals to steal credit card information and place false orders in your business. Here is a step-by-step guide to secure your eCommerce business.
Step 1: Promote the use of strong, unique passwords
According to the Verizon Data Breach Investigations Report for 2020, stolen or weak credentials were utilized in 37% of credential theft breaches. It’s worth ensuring your employees and customers follow these password best practices:
- Strong passwords contain upper and lowercase letters, digits, and symbols and are at least eight characters long.
- You should never ever share your password; each user should have a separate username and password for logging in. Using a reliable password manager can simplify this process by securely storing and managing all your passwords, ensuring they remain strong and unique across different platforms.
- Encourage users and your team to use different passwords for different login credentials than you do for other websites. Consider using a password management tool as an extra layer of security.
Step 2: Use HTTPS hosting
Secure HTTPS hosting which necessitates the use of an SSL (Secure Sockets Layer) certificate, will aid in the security of your website.

SSL is a technology standard that establishes an encrypted connection between a web server or host and the web browser or client. This makes sure the data passing between the two remains private. Websites that use SSL will have “https://” in the address bar next to their domains. As a result, SSL helps establish trust with paying customers, especially for protecting your eCommerce security.
Because Google penalizes websites with HTTP in organic search rankings, it’s also a windfall for your marketing department. HTTPS delivers a favorable trust signal to your customers, especially those who are tech-savvy.
Step 3: Protect your devices
Make sure your connected devices are cyber safe with anti-virus software, firewalls, or another appropriate technique of safeguarding against attacks, whether you have one computer in a home office or a headquarters with a fully networked computer system.
You can also use a VPN for an extra layer of protection and security when accessing sensitive data online. You can also use some virtual data rooms to safely protect your data online.
Step 4: Defend yourself against attempts at social engineering
Avoiding phishing traps is one of the most effective strategies to prevent malware infections. Never give out any personal information without verifying the recipient’s identification first.
Keep in mind that never open links in questionable emails because they may lead to a webpage that seems like a legitimate login page. However, the truth is that this webpage will steal your personal information in some ways. Also, avoid downloading any attachments that you weren’t anticipating.
The same is true of any URLs you might visit. They may appear legitimate at first sight, but the spelling may be incorrect by one letter in the hope that you will not notice and click on the harmful URL. Suspicious emails may ask you to do something urgently, such as transfer money or authorize a charge.
Step 5: Protect your domain with email authentication protocols
SPF, DKIM, and DMARC are standards that help different aspects of authentication to ensure that your domain is safe. These 3 protocols work together and complement each other’s function. Their mission is to protect your domain from any criminal trying to impersonate you by sending phishing and spoofing emails.
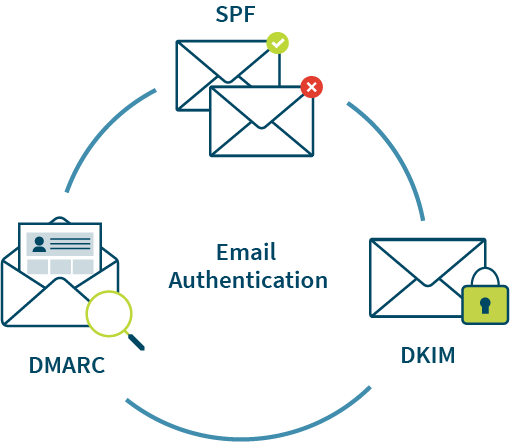
- DMARC stands for Domain-based Message Authentication, Reporting & Conformance. DMARC records allow Internet Service Providers (ISPs) to prevent malicious email practices.
- SPF stands for Sender Policy Framework. SPF records show the mail servers that are allowed to send emails from your domain. SPF flattening, in its turn, replaces all the domains in your SPF record with their appropriate IP addresses. A quick SPF record check can show you the record published in DNS for your domain so you can detect anomalies if any.
- DKIM stands for DomainKeys Identified Mail. This email security standard helps make sure emails are not tampered with while moving from the sender and the receiver servers. As an email leaves the sending server, DKIM employs public-key cryptography to sign messages with a private key to ensure its legitimacy.
Step 6: Implement additional authentication
Although it may seem cumbersome sometimes, employing 2-step verification, two-factor authentication, or multi-factor authentication ensures that only you and your authorized users are logging into your store. It’s worth it when you consider the potential ramifications of a breach.
Step 7: Keep useful information about your customers
When it comes to data storage, be it in the form of VDR or cloud, you should never keep more than you need to run your organization efficiently. With the increasing number of data privacy requirements, it’s more necessary than ever to carefully design your company’s philosophy in order to strike a balance between customer experience, business convenience, and cloud security.
So, make sure you don’t store any unnecessary data. Also, clean your Mac PC, especially its system data, or any other device, from time to time while using their physical storage to save important customer data. This will help in saving only the required data and removing any duplicate or unwanted ones.
Additionally, segment your network to keep your clients’ vital data separate from unrelated information. You’d better install firewalls and do audits to ensure that all of your security measures are working as they should. Maintaining optimal security is vital when it comes to storing and managing sensitive data such as customer information. Ensure that all network and cloud security measures are sufficient to protect this data from hackers and other security breaches – failure to do so could make or break your company’s reputation.
Step 8: Make sure your website is up to date
Security is a never-ending game of cat and mouse. Sooner or later, attackers will find out the vulnerabilities from your system, and they will be patched by the best board portal software experts. Updates to your software are handled automatically if you use a SaaS eCommerce platform.
However, your company is responsible for executing any software updates, bug fixes, or vulnerability patches with on-premises eCommerce systems.
Step 9: Review all plugins and third-party integrations on a regular basis
Review and make a list of the third-party applications you use. Make sure you understand what they are and evaluate your level of trust in that third party. Remove the integration from your store if you’re no longer utilizing it. The goal is to give as few people as possible access to your clients’ data while yet moving your company ahead.
Step 10: Backup your data
In the event of losing your data and you can’t access it, you’ll need backup files to get your business back to work and running as quickly as possible.
Step 11: Make sure your customer service team is ready
You and your staff sure need to be well-prepared for typical hazards, such as having a clear verification process in place to confirm the identity of consumers who seek modifications to their purchases or accounts.
Step 12: Prepare a security update strategy
To prevent additional danger, it’s a good idea to lock down your store completely for the holidays and make no changes. However, when it comes to security and patching your website for any flaws, that general rule does not apply. This is particularly relevant in case you’re using an on-premise eCommerce solution. To safeguard the security of your business and your customers, you should have a tried-and-true process in place for site updates whenever they become necessary.
Conclusion
Developing strong eCommerce security is critical to a company’s success. Bear in mind that you can’t afford to lose your consumers’ trust by revealing personal information. You’d better spend more time building your business and less time worrying about security monitoring and maintenance just following these tips.
If you follow the advice in this post and stay informed about your cybersecurity world, You can give your consumers a secure shopping experience.