It’s no secret why the WordPress platform is often preferred over other CMS platforms. Its easy-to-use interface, flexibility, and simple set-up ensure its popularity. However, this popularity has also compromised quite a number of WordPress sites and led to data breaches, placement of malware, and exploitation of plugin/theme vulnerabilities.
Keeping security at the forefront of your approach benefits not just your efforts, but your customers as well. The ideal user experience is ensuring optimal services along with security from malicious elements. Therefore, when you implement new WordPress plugins and/or themes, there are certain security considerations that need to be taken care of before you push your theme or plugin into the production stage.
In this article, let’s go through several steps to perform WordPress plugin and theme security audit to ensure a high level of security for your eCommerce store.
Without further ado, let’s get this show on the road.
Plugin and Theme Security Audit – Why Do You Need It?
Ask any WordPress site owner or follow the statistics of the most common WordPress attacks, you’ll understand why it’s crucial to address the plugin and theme vulnerabilities. A shocking 70 million WordPress sites are running on vulnerable plugins and themes, causing more than 50% of WordPress attacks. The resulting damage and data loss also have long-term impacts on the site’s reputation, no matter how useful it was.
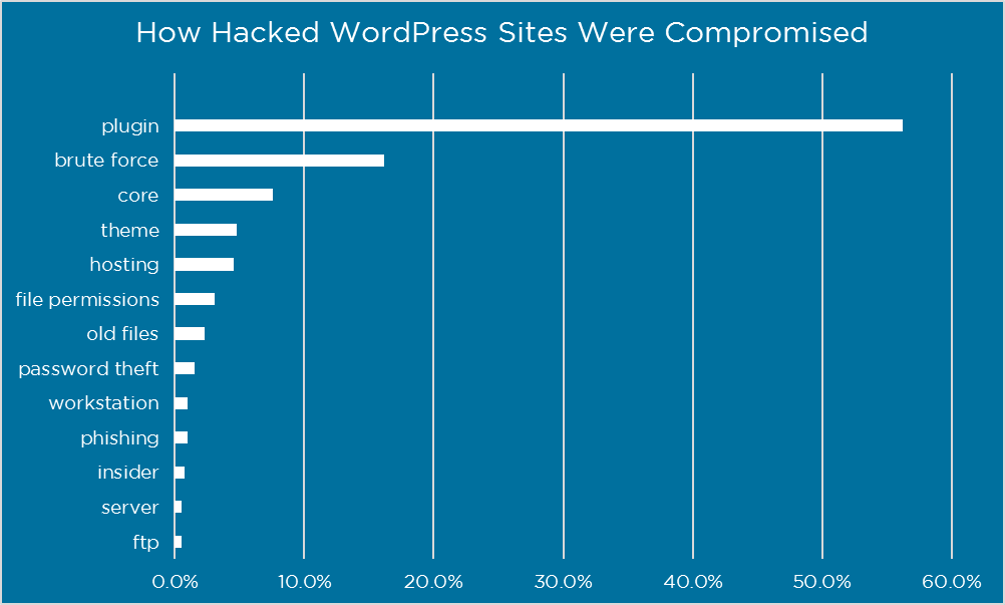
Also referred to as plugin vulnerability assessment and penetration testing (VAPT), this process involves a team of cybersecurity professionals looking into the possibility of security risks. This includes testing for misconfiguration issues, point of entry attacks, and other exploitation possibilities. The vulnerability assessment detects the security risks and potential points of escalation, and the penetration testing simulates attack scenarios to test for full impact.
Also referred to as plugin vulnerability assessment and penetration testing (VAPT), this process involves a team of cybersecurity professionals looking into the possibility of security risks. This includes testing for misconfiguration issues, point of entry attacks, and other exploitation possibilities. Software testing services can play a vital role in ensuring the security and functionality of your plugins and themes, thereby enhancing the overall performance of your website.
Here are a few more reasons why a plugin and theme security audit are crucial to the WordPress security strategy:
- Initiate phishing attacks against your customers;
- Malicious code injection from the MySQL database, SEO spam, and cross-site scripting (XSS) attacks that may lead to website blacklisting;
- Loss of customer data such as payment information, personal details, etc;
- Encrypt site data in an unrecognizable manner and ask for ransom for its solution.
Conducting a Plugin and Theme Security Audit
Now that we’ve covered the ‘why’, let’s move to the ‘how’. These are the steps you need to follow to ensure a comprehensive security audit for your themes and plugins.
Data validation, clean-up, and data escaping
Data validation involves checking the data input and comparing it with known patterns to recognize issues. The clean-up or sanitation process usually involves cleaning this data and filtering out problems.
It’s important to sanitize and verify data such as API-based calls for services and other user input. Any loopholes will allow hackers to input malicious content, which is one of the most common exploitation techniques. Tools that allow you to test theme security with this method are QuerySurge, Data gaps ETL Validator, etc.
The process of data escaping removes unnecessary data such as script tags and incomplete HTML so that it isn’t seen as code. Proper escaping is an important step before the data is rendered for the end-user, especially for avoiding XSS attacks.
Accounting for injection attacks
Using a simply modified SQL query, hackers can access your database and manipulate the data or insert malicious code.In 2020, SQL injection vulnerabilities remain the topmost concern for over a million custom WordPress websites. These kinds of attacks commonly occur through fields that accept user input with the hacker inserting SQL code and customizing the request sent to the database.
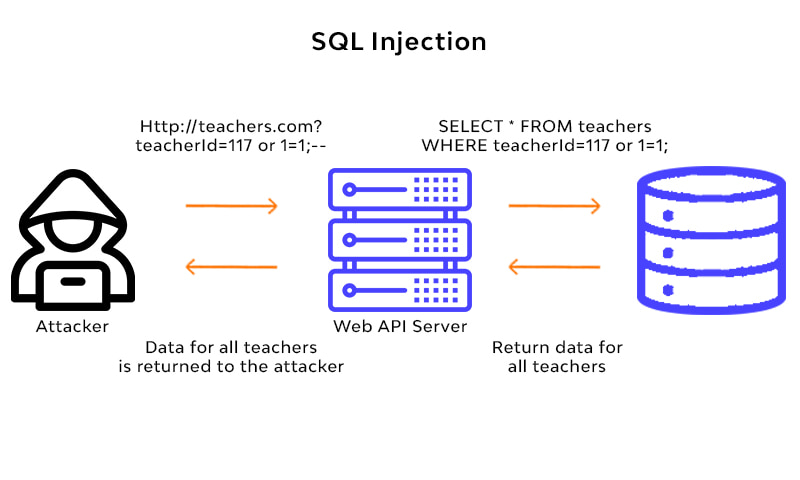
As part of your auditing process, sending blind SQL attacks and running the code on your database will reveal vulnerabilities related to adding new administrators, removing data, etc. They could be random parts of the SQL code send as part of the query. You can then detect any changes initiated to the website output and uncover the potential for injection attacks.
Check if the plugin developer has used the built-in database class available on WordPress ‘$wpdb’. This allows you to interact with the database and use its functions safely. Input should be properly sanitized, as mentioned in the first step, to only accept the exact data type (letters in the case of names).
Check the ‘container’
Sometimes, a container-based technology is used for hosting multiple environments for development purposes. In this case, it’s important that appropriate scanning and analysis are done to ensure security. This should include the images in the container, compliance requirements, security keys, and any malware or vulnerabilities that may be present.
This is why third-party plugins and themes shouldn’t be trusted too much. If any are implemented, there should be regular checks for updates. The software integration involved for such a theme/plugin has the potential to introduce new vulnerabilities in the container’s environment.
Conducting SAST, DAST, and IAST
The Static Application Security Testing (SAST) process allows you to test and go through your code and search it for vulnerabilities. Since it’s done from the inside, it’s also referred to as white-box testing. It helps you to find and resolve any issues in the software development life cycle (SDLC).
The Dynamic Application Security Testing (DAST) checks the strength of the system mid-attack including the themes and containers. This form of black-box testing provides a different list of vulnerabilities and is usually done with a DAST scanner.
The Interactive Application Security Testing (IAST) tests in a combination of SAST and DAST, analyzes more code, and implements wider security. It’s a grey-box testing procedure that covers more hidden files, configuration details, etc. IAST tools can be used both during the production process and in real-time.

The SAST, DAST, and IAST process done for auditing a theme or plugin is mostly similar to conducting a web application security testing.
The nonce system in WordPress
Nonce or the ‘number only used once’ system, adds a unique number to the request to the WordPress install from your source code. The actual process involves regenerating the nonce term and not just a unique assignment. This helps you in identifying the legitimacy of the request and is implemented as a measure of security in most plugins.
Therefore, ensure that the nonce system is active on your site, which generates the JavaScript files and produces a unique combination of lower and uppercase letters as well. When the JavaScript code sends the request, this code is sent along with it – if it doesn’t match the phrase, your source code should be able to ignore it completely.
Using the Software Composition Analysis (SCA) tool
If there are public vulnerabilities in the code imported/outsourced from outside the organization, this tool helps you test them. OWASP provides a dependency-check tool that goes through outdated code and other vulnerabilities when placed in your development environment. This stage is important because most of the time, the code isn’t usually checked beyond the static analysis phase.
Conduct background checks
It’s important to evaluate the developers before installing their plugins or themes. Always check the installation figures and other plugins released by the same entity to assess their quality in the market. How active the developer is can help you decide if they regularly release updates and security patches when vulnerabilities are discovered. Check out their terms of service and privacy policy to ensure legitimacy.
Go through the product review and ratings to gain a proper assessment of the kind of services and quality offered by the product. Even if it’s placed in the official repository, users leave star ratings to indicate their experience. Keep checking the feedback in case any concerns on security are flagged and if it has led to the overall drop in the product rating.
Verify the presence of developer support for your chosen themes and plugins. These components on WordPress contain the most vulnerabilities, which usually focuses the attention of developers on discovered and potential issues, and makes them release security patches for the same. Product pages usually contain a portion that maintains a track record of the number and kind of upgrades implemented. There’s also a special mention by WordPress if the plugin has been tested with the CMS’ previous three major upgrades. If there’s a lack of recent updates, avoid installing the product and look into other options.
Finally, look into the responses of the developer to queries and concerns of the product’s users. The high-quality developers will remain easily contactable and provide multiple ways of reaching out to them, with prompt answers and useful feedback.
Updates
Perform WordPress update regularly is very important to deal with the hidden vulnerabilities, improve overall performance and adaptability. It also ensures that your plugins and themes are updated to their latest versions to avoid having backdoors for manipulation. The option for updates lies under the ‘Dashboard > Updates’.
These are a few of the steps taken during a plugin and theme security audit. After completion of the security audit, it is important to make a security audit or penetration testing report which can help you keep a record of findings and remediation steps taken to fix those findings.
Conclusion
Each organization has its unique security needs, so there may be some additions to the procedure of plugin and theme security audit, it is recommended that you scope the plugin and theme security audit according to the business goal.
Wanting to move to a more secured eCommerce platform? Please consider choosing LitExtension – the #1 shopping cart migration expert. With our 24/7 support team, LitExtension will ensure a fast, secure, and accurate migration process for your store.
Last but not least, don’t forget to join our Facebook Community to get more eCommerce tips and news.